This is something that I never like to see but if you head on over to TeenDomainer.com you’ll see the following page:
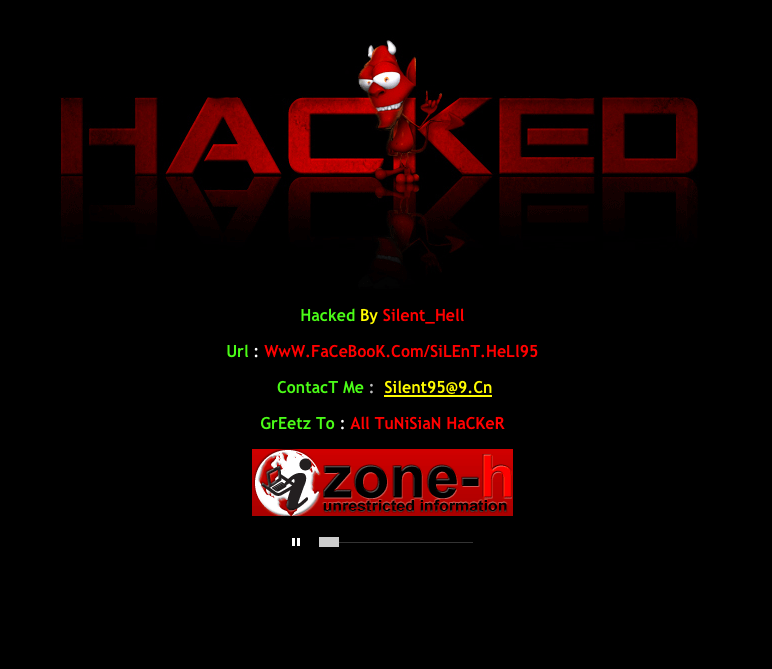 It appears that a hacker going under the name “Silent_Hell” has somehow gained access to Brian’s server/Wordpress Install and put-up this page. As someone that has had many sites hacked over the years I know how frustrating this is and I am reaching-out to Brian to help-out.
It appears that a hacker going under the name “Silent_Hell” has somehow gained access to Brian’s server/Wordpress Install and put-up this page. As someone that has had many sites hacked over the years I know how frustrating this is and I am reaching-out to Brian to help-out.
I have found that many of these hackers have .CN or .RU email addresses and can be very hard to track-down. This is one of the main reasons I use VaultPress which is a great WordPress plugin that constantly backs-up your blog when something like this happens.
While I will be lending a hand today I would also like to reach-out to any of my readers that have experience fixing hacked sites along and tracking down hackers like this. Brian is a really nice guy and TeenDomainer.com is one of my favorite blogs in our space so it’s always sad to see something like this happen to someone that is doing so much good for our community. If you want to lend a hand or have some expertise that might come in handy please comment below and I’ll pass your information along to Brian.