Welcome to the second week of WordPress for Geeks and a topic that all geeks absolutely need to know, how to tell if your WordPress site has been hacked. Back in the 90’s and early 2000’s hacking a site meant completely changing the landing page often replacing it with a scull and crossbones. Now hackers are often much more interested in your link juice than the victory of letting you know that your site has been compromised. In fact, their hope is that you never notice so you can keep giving them valuable link juice for nothing.
One of the most common attacks on a WordPress installation is spam link injection. This is often done once a hacker gains access to your site due to an insecure plugin or out of date WordPress installation. Once inside they add links back to their site, but these links often hard to spot so you might not find out about the injection until weeks, months or even years after it happens, unless you’re a geek. Since this is WordPress for geeks that’s exactly what we’re going to teach you how to do.
The first thing you want to do as a good WordPress Geek is constantly know when any of your important files change. To do this you’ll want to install WordPress File Monitor. It’s a free plugin that I’ve used for a long time and if someone makes any changes to your WordPress files, you’ll know right-away.
So how can you tell if someone has injected spam links into your WordPress installation if the links don’t show up directly in WordPress? Put up your geek antennas, we’re moving onto level two. You will need to use the WordPress file editor and search through your WordPress theme files looking for something with the “eval” command which is used to run an executable. It is this executable that is run through one of your PHP files that injects the spam links, but it’s completed encoded so what you see will look like a bunch of gabaly goop. Technically what is happening here is external Javascript code is being decoded with a base 64 decode.
Below is an example of what you’ll most likely see if your site has been compromised:
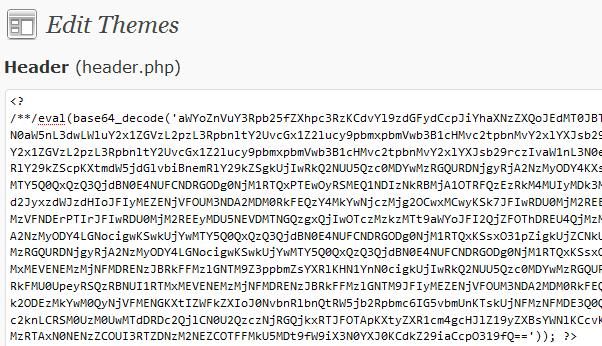
If you see this, don’t panic. Luckily you’re not the first person to be hit by this kind of attack so plenty of work has been done to remove the malicious code and get your site back to normal. The easiest way to solve the problem is to backup your database and then install a fresh copy of WordPress. Then load your new database into the new install of WordPress that is now free of the malicious code. You can read a more detailed description of how to rid your installation of spam injection links in one of my personal favorite articles, How To Completely Clean Your Hacked WordPress Installation.
Last but not least, in some cases hackers can get into your WordPress database which means copying it over won’t do a ton of good. In this case I’d look for an expert who knows MySQL and can easily look for errors in your database and get things back to tip top shape. So don’t wait until your site is magically de-listed from Google, start looking right away and make sure your blog has not been compromised. If it has remember, don’t panic, just solve the problem! You are now a bit geekier than you were last week, feel any different?